Breaking the Waves
a workshop by Gordan Savičić and Danja Vasiliev
Encrypted Wi-Fi networks are private spaces carrying simple radio waves into the ether. Still, they can be received with normal equipment in public space, far beyond your apartment’s room. Who and what is claiming the ether? Are waves an emerging transmission carrier reshaping the definition of public and private space?
Sometimes we can still enjoy the luck of finding an open Wi-Fi network that some generous geek left free or occupied house-wife forgot to secure. Sadly, most recent wireless access points come off the shop shelves being pre-configured with rather strong encryption. We believe that regardless the settings the devices sold with, people still might not mind us using their wireless for the common good. All we need to do is to help them share it.
On another hand the concept of wireless security is a flaky topic to begin with. Anything what is in the air (like the radio waves) can be captured and decoded. There are no barriers for anyone to tap into anyone else’s radio network and with the power of modern computers cracking the encryption takes very symbolic time to complete.
The workshop showcases the ease of cracking WEP/WPA wireless network encryptions as a way for understanding the risks of Wi-Fi networks and will provide participants with handy computer skill for the precarious offline times. After the participants taught the easy ways of securing your own wireless environment.
———————————————————————————————————————–
photos from the workshop
12. 06. 2011.

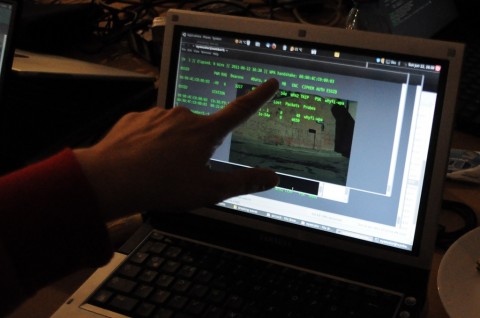
Data Carving
a workshop by Gordan Savičić and Danja Vasiliev
During the “Data carving” workshop, participants will explore the contents of found hard-disks. Using methods borrowed from computer digital forensics participants will peek into the lives of others – former owners of scavenged hardware. Hard-disks as the most intimate part of any computer system. In case of a personal computer – the most intimate part of person’s life. Deductively, we will try to discuss and recreate “psyche” portraits of those strangers and restore the time-lines that otherwise would have faded away. In the times of paranoiac privacy awareness we forget that online is not the only place to loose your identity. Although more and more personal data is stored on the Internet servers it is still written to hard-disks. There were several reports about Internet servers hard-disks ending up on flea-markets, being sold for cheap money.
————————————————————————————————————————
photos from the workshop
11. 06. 2011.



Navigate me
a workshop by Darija Medić
This workshop will demonstrate the possibilities to use GPS software and hardware for playing with different referential systems; Participants will work with locative media in urban environment and examine their abilities to navigate through the physical space of information.
—————————————————————————————————————————
pictures from the workshop
10. 06. 2011.


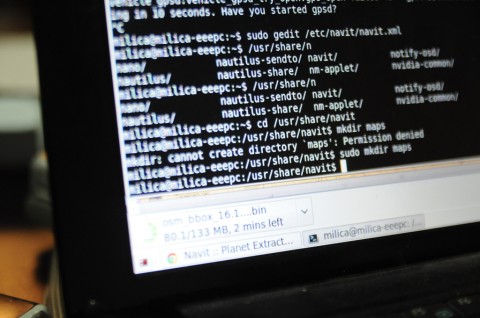
Text Only
a workshop by Maria Karagianni (Genderchangers)
Introduction to the command line, interaction with the computer throught textual commands only
The “Text Only” workshop will introduce participants to interacting with the computer operating system from a command line interface. In Windows terminology one would run a DOS “box”, while in Linux and Mac OS X the terminal window gives access to a prompt from which to send commands to the computer. The more familiar one gets in this text only environment the more you can do with your computer.
—————————————————————————————————————————
photos from the workshop
13. 06. 2011.

